Blog Posts
- Home /
- Blog Posts
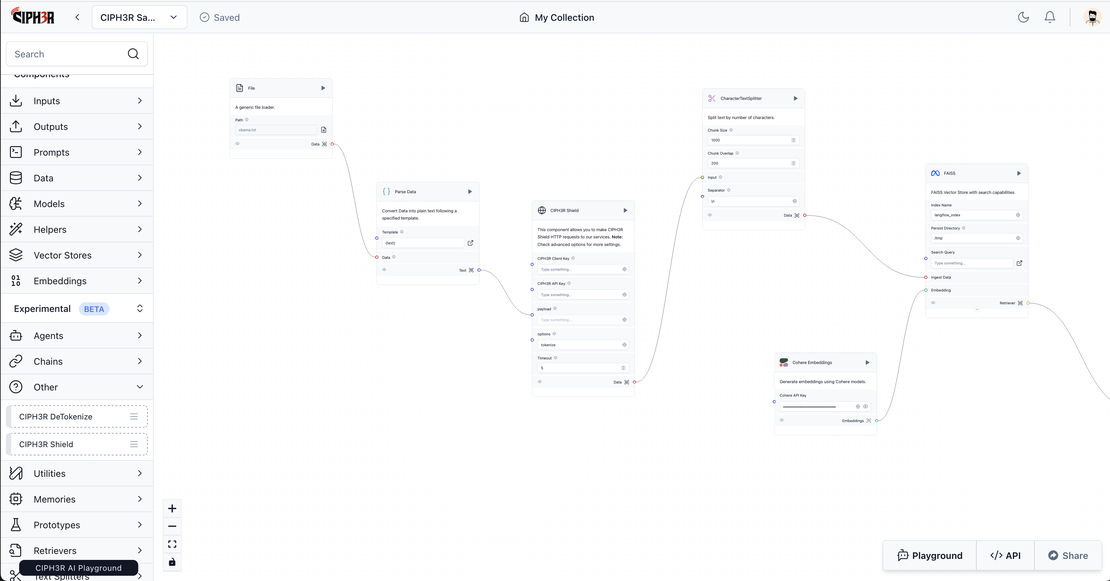
How to use CIPH3R Playground Components to detect PII
Components There two CIPH3R AI Playground components:- CIPH3R Shield CIPH3R Detokenize
Read More
OFSI B-13 Compliance through Format-Preserving Encryption (FPE)
Title: Aligning with OSFI B-13 Compliance through Format-Preserving Encryption (FPE)
Read More
Strengthening Quebec's Law 25 or Bill 64 Compliance with CIPH3R’s FPE
Format-preserving encryption (FPE) serves as a valuable tool for organizations seeking to comply with Quebec’s Bill 64, also known as Law 25. Law 25 establishes comprehensive data protection standards for businesses operating in the province. Non-compliance with Law 25 can result in significant fines. This blog post explores how FPE empowers organizations to effectively navigate these data privacy regulations.
Read More
Ensuring CCPA Compliance with CIPH3R’s FPE Solutions
In the realm of data privacy and protection, compliance with the California Consumer Privacy Act (CCPA) stands as a critical obligation for organizations operating in California. This legislation sets forth stringent requirements for the handling and safeguarding of personal data, imposing significant penalties for non-compliance. To navigate the complexities of CCPA effectively, organizations turn to Format-Preserving Encryption (FPE) as a pivotal tool. Here’s how CIPH3R’s FPE solutions can facilitate CCPA compliance:
Read More
Gen AI Privacy: Storing PII efficiently in Vector DB using FPE
In our previous blog Gen AI Data Privacy, we demonstrated the practical applications of Langchain Document Loader. In this installment, we delve into the seamless integration of this tool with Vectordb, a popular database solution. Additionally, we will explore its compatibility with blockchain technology, ensuring secure and private access to Language Model (LLM) responses.
Read More
Achieving ISO Compliance with CIPH3R’s FPE
Format-preserving encryption (FPE) can be a valuable tool for helping organizations achieve compliance with various ISO (International Organization for Standardization) standards, depending on the specific standard and the organization’s needs. ISO standards cover a wide range of topics, including information security, data privacy, and quality management. Here’s how FPE can contribute to ISO compliance in some key areas:
Read More
Achieving SOC1, SOC 2, and SOC 3 Compliance with CIPH3R’s FPE
In the landscape of regulatory compliance, adherence to SOC 1, SOC 2, and SOC 3 frameworks is paramount for organizations striving to uphold the highest standards of data security and integrity. Format Preserving Encryption (FPE) emerges as a pivotal technology, offering a seamless solution to achieve and maintain compliance across these stringent frameworks. Let’s delve into how FPE enables organizations to navigate the complexities of SOC 1, SOC 2, and SOC 3 compliance with precision and efficacy.
Read More
AI Data Privacy: Classify and Encrypt Data using CIPH3R FPE before Integrating with Gen AI
Prior to embarking on the integration and utilization of Generative AI within your organizational framework, it is imperative to establish and implement an AI Use Policy. This policy serves to delineate the permissible access to internal data by AI models and provides guidance on the integration process, particularly in instances involving Personally Identifiable Information (PII) data.
Read More
Achieving PIPEDA Compliance with CIPH3R’s FPE
Format-preserving encryption (FPE) can be a valuable technology for helping organizations achieve compliance with the Personal Information Protection and Electronic Documents Act (PIPEDA) in Canada. PIPEDA sets the standards for the collection, use, and disclosure of personal information in the private sector. Here’s how FPE can contribute to PIPEDA compliance:
Read More
Is your Vector Database unsafe?
The promise of vector databases (VDBs) is undeniable. Lightning-fast processing, intuitive analytics on complex data, and unlocking the power of AI applications – it’s a data scientist’s dream. But lurking beneath the surface, a silent threat can turn this dream into a security nightmare: the vulnerability of unprotected data.
Read More